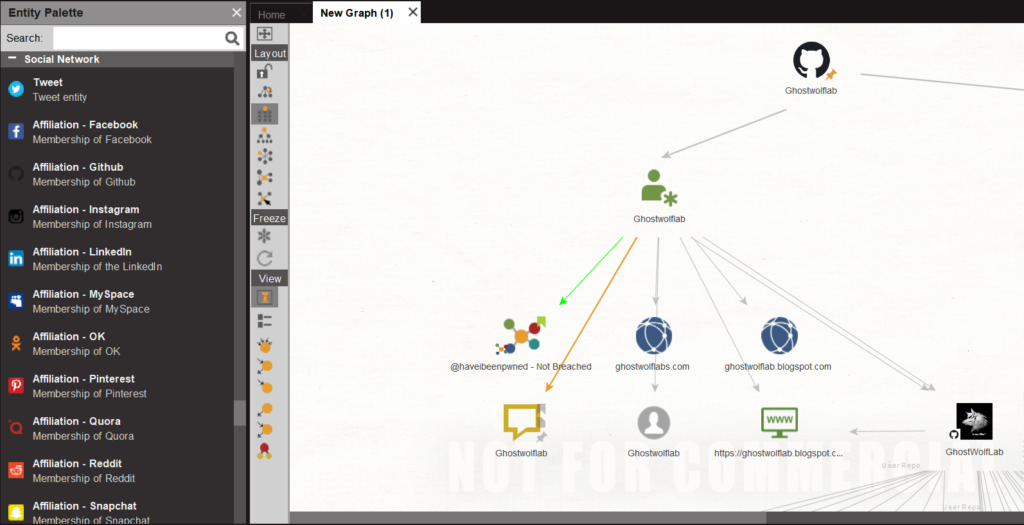
综合侦察工具
10 months ago
5 minutes
Amass
深入的攻击面映射和资产发现
# https://github.com/owasp-amass/amass
amass enum -passive -d 域名 -src
amass enum -active -d 域名
amass enum -v -src -ip -brute -min-for-recursive 2 -d 域名
amass viz -d3 -d 域名
IVRE
IVRE 是一个用于网络侦察的开源框架
apt install ivre ivre-doc
ivre ipinfo –init //初始化IP地址信息
ivre scancli –init //初始化主动扫描数据库
ivre view –init //初始化视图信息
ivre flowcli –init //初始化数据流信息
sudo ivre runscansagentdb –init //初始化远程代理扫描
ivre ipdata –download //下载IP地址数据
ivre runscans --routable --limit 100 --output=XMLFork --processes 10
//运行10个并发Nmap进程来枚举随机100个IP地址
ivre scan2db -c ROUTABLE-001 -s MySource -r scans/ROUTABLE/up
//分析Nmap的扫描结果并将其添加到数据库中
ivre db2view nmap
//从Nmap扫描结果和被动侦查的数据库中创建视图
ivre scancli –count
//统计数据
ivre httpd --bind-address 0.0.0.0
//启动WEB图形化显示
rm -rf scans/ROUTABLE/*
//清除测试数据
ivre scancli --init && ivre view –init //数据初始化
ivre runscans --routable --categories 自定义分类名 --network 网段 --output=XMLFork --processes 10 //自定义网段扫描
ivre scan2db -c 自定义分类名 -s 扫描源 -r scans/自定义分类名/up
ivre db2view nmap
ivre httpd --bind-address 0.0.0.0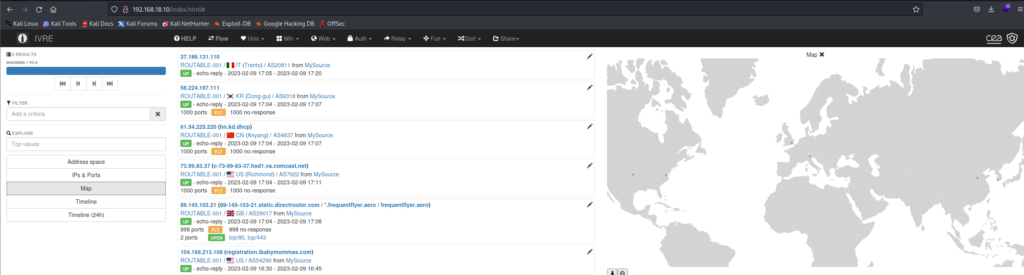
Rengine
用于 Web 应用程序的自动化侦察框架,重点是通过引擎进行高度可配置的简化侦察流程、侦察数据关联和组织、持续监控、由数据库支持以及简单而直观的用户界面。
下载地址:
# https://github.com/yogeshojha/rengine
快速入门:
# https://rengine.wiki/getting-started/#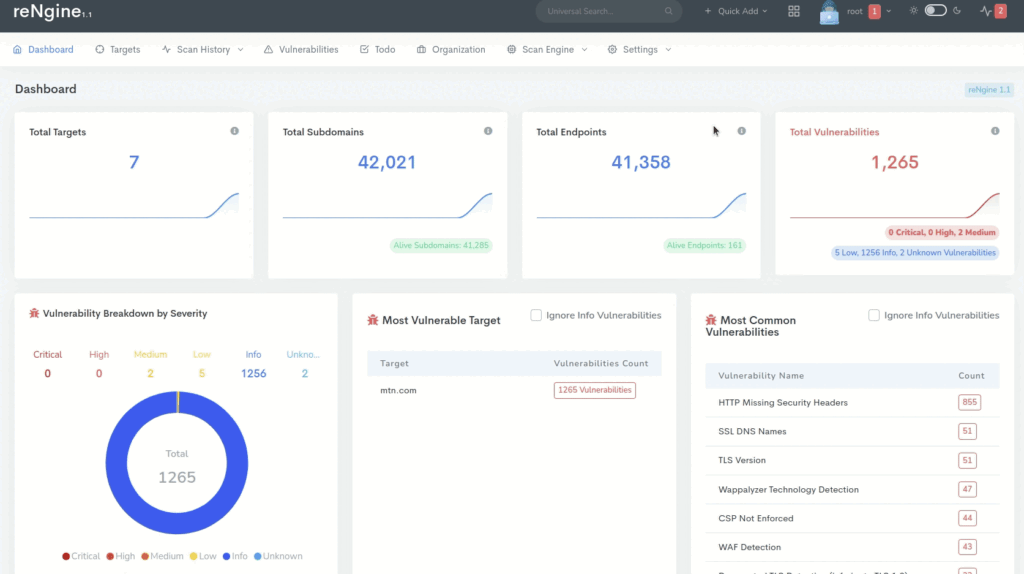
Osmedeus
用于进攻性安全的工作流引擎
# https://github.com/j3ssie/Osmedeus
# go install -v github.com/j3ssie/osmedeus@latest
用法:
# Example Scan Commands:
## Start a simple scan with default 'general' flow
osmedeus scan -t sample.com
## Start a general scan but exclude some of the module
osmedeus scan -t sample.com -x screenshot -x spider
## Start a scan directly with a module with inputs as a list of http domains like this https://sub.example.com
osmedeus scan -m content-discovery -t http-file.txt
## Initiate the scan using a speed option other than the default setting
osmedeus scan -f vuln --tactic gently -t sample.com
osmedeus scan --threads-hold=10 -t sample.com
osmedeus scan -B 5 -t sample.com
## Start a simple scan with other flow
osmedeus scan -f vuln -t sample.com
osmedeus scan -f extensive -t sample.com -t another.com
osmedeus scan -f urls -t list-of-urls.txt
## Scan list of targets
osmedeus scan -T list_of_targets.txt
osmedeus scan -f vuln -T list-of-targets.txt
## Performing static vulnerability scan and secret scan on a git repo
osmedeus scan -m repo-scan -t https://github.com/j3ssie/sample-repo
osmedeus scan -m repo-scan -t /tmp/source-code-folder
osmedeus scan -m repo-scan -T list-of-repo.txt
## Scan for CIDR with file contains CIDR with the format '1.2.3.4/24'
osmedeus scan -f cidr -t list-of-ciders.txt
osmedeus scan -f cidr -t '1.2.3.4/24' # this will auto convert the single input to the file and run
## Directly run on vuln scan and directory scan on list of domains
osmedeus scan -f domains -t list-of-domains.txt
osmedeus scan -f vuln-and-dirb -t list-of-domains.txt
## Use a custom wordlist
osmedeus scan -t sample.com -p 'wordlists={{Data}}/wordlists/content/big.txt'
## Use a custom wordlist
cat list_of_targets.txt | osmedeus scan -c 2
## Start a normal scan and backup entire workflow folder to the backup folder
osmedeus scan --backup -f domains -t list-of-subdomains.txt
## Start the scan with chunk inputs to review the output way more much faster
osmedeus scan --chunk --chunk-parts 20 -f cidr -t list-of-100-cidr.txt
## Continuously run the scan on a target right after it finished
osmedeus utils cron --for --cmd 'osmedeus scan -t example.com'
## Backing up all workspaces
ls ~/workspaces-osmedeus | osmedeus report compress
# Scan Usage:
osmedeus scan -f [flowName] -t [target]
osmedeus scan -m [modulePath] -T [targetsFile]
osmedeus scan -f /path/to/flow.yaml -t [target]
osmedeus scan -m /path/to/module.yaml -t [target] --params 'port=9200'
osmedeus scan -m /path/to/module.yaml -t [target] -l /tmp/log.log
osmedeus scan --tactic aggressive -m module -t [target]
cat targets | osmedeus scan -f sample
# Practical Scan Usage:
osmedeus scan -T list_of_targets.txt -W custom_workspaces
osmedeus scan -t target.com -w workspace_name --debug
osmedeus scan -f general -t sample.com
osmedeus scan --tactic aggressive -f general -t sample.com
osmedeus scan -f extensive -t sample.com -t another.com
cat list_of_urls.txt | osmedeus scan -f urls
osmedeus scan --threads-hold=15 -f cidr -t 1.2.3.4/24
osmedeus scan -m ~/.osmedeus/core/workflow/test/dirbscan.yaml -t list_of_urls.txt
osmedeus scan --wfFolder ~/custom-workflow/ -f your-custom-workflow -t list_of_urls.txt
osmedeus scan --chunk --chunk-part 40 -c 2 -f cidr -t list-of-cidr.txt
💡 For full help message, please run: osmedeus --hh or osmedeus scan --hh
📖 Documentation can be found here: https://docs.osmedeus.orgSpiderFoot
自动化 OSINT 以获取威胁情报并绘制攻击面图
git clone https://github.com/smicallef/spiderfoot.git
cd spiderfoot
pip3 install -r requirements.txt
python3 ./sf.py -l 127.0.0.1:5001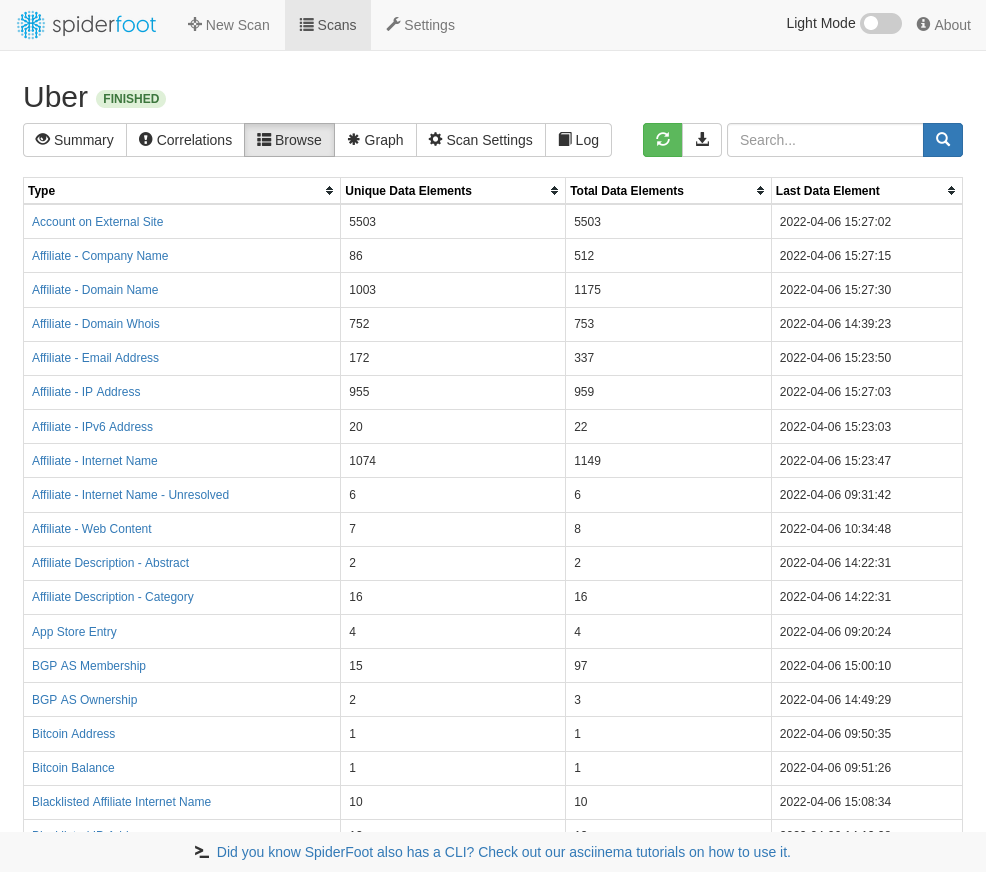
theHarvester
电子邮件、子域名和域名的OSINT工具
theHarvester -d target.com -b google,bing,baidu,bufferoverun,crtsh,dnsdumpster,duckduckgo,github-code,hackertarget,netcraft,rapiddns,rocketreach,sublist3r,trello,urlscan -n -r -v -s --screenshot target/harvester -g Maltego
最经典的图形化框架的信息收集工具,官网: